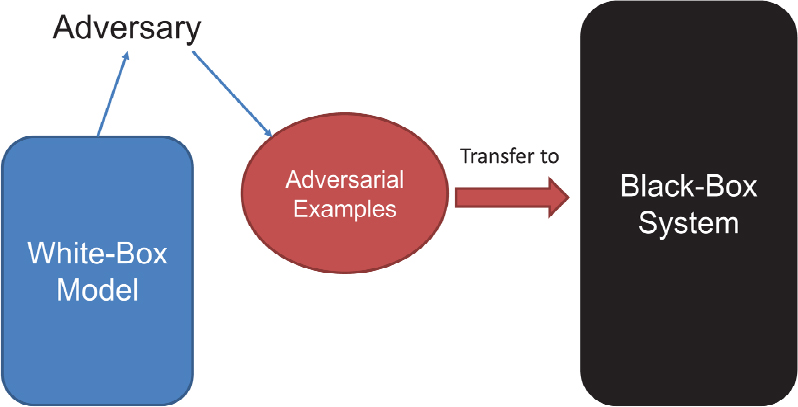
7 Plenary Session | Robust Machine Learning Algorithms and Systems for Detection and Mitigation of Adversarial Attacks and Anomalies: Proceedings of a Workshop | The National Academies Press
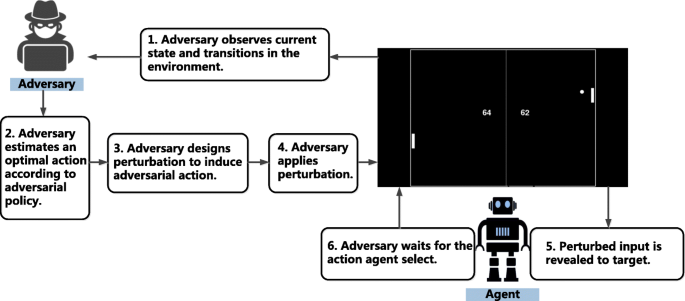
Adversarial attack and defense in reinforcement learning-from AI security view | Cybersecurity | Full Text
![PDF] ZOO: Zeroth Order Optimization Based Black-box Attacks to Deep Neural Networks without Training Substitute Models | Semantic Scholar PDF] ZOO: Zeroth Order Optimization Based Black-box Attacks to Deep Neural Networks without Training Substitute Models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9ab7319dbe80549ba80e3320d0546d741a7a5791/3-Figure2-1.png)
PDF] ZOO: Zeroth Order Optimization Based Black-box Attacks to Deep Neural Networks without Training Substitute Models | Semantic Scholar

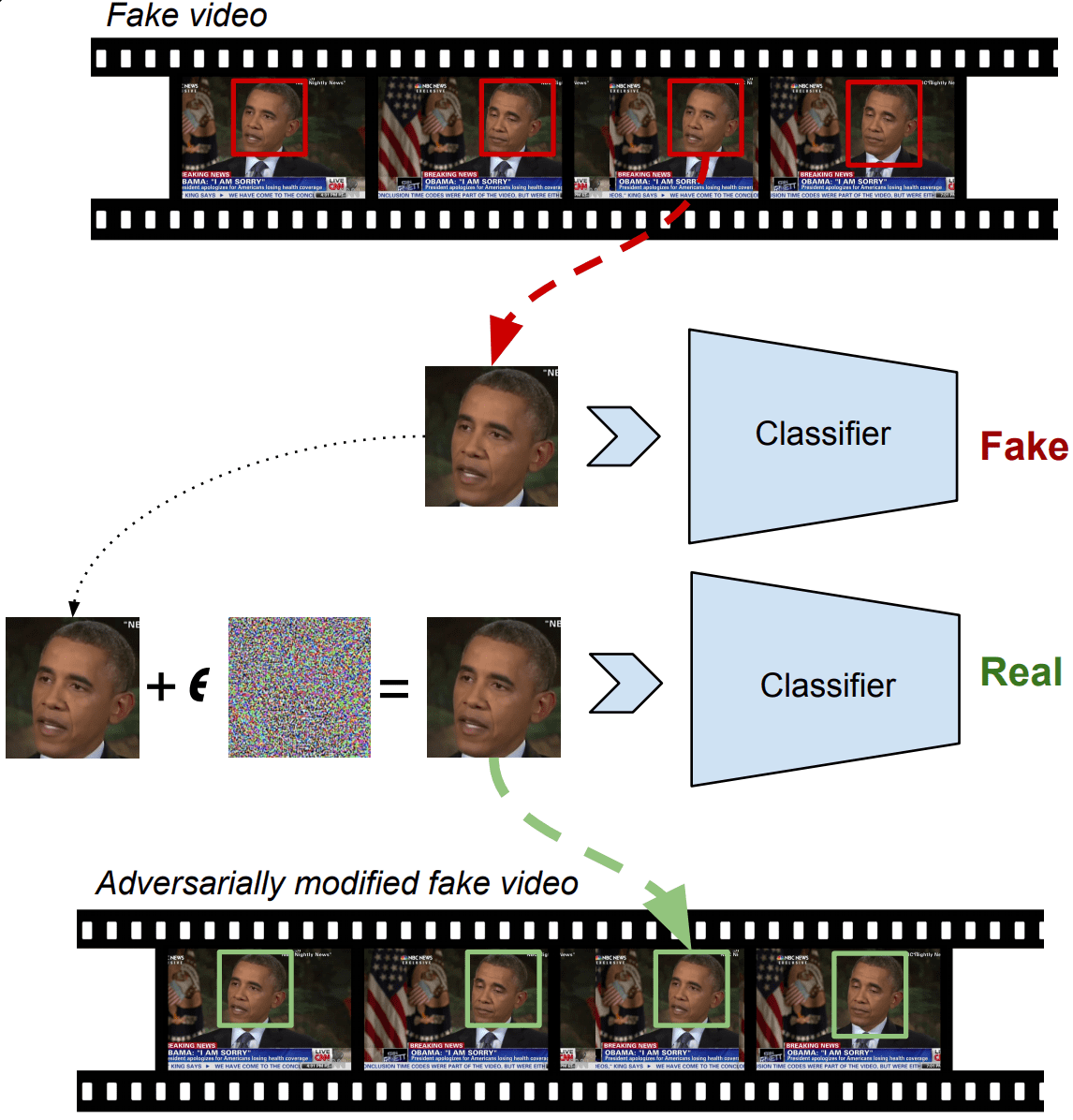
Tricking a Machine into Thinking You're Milla Jovovich | by Rey Reza Wiyatno | Element AI Lab | Medium
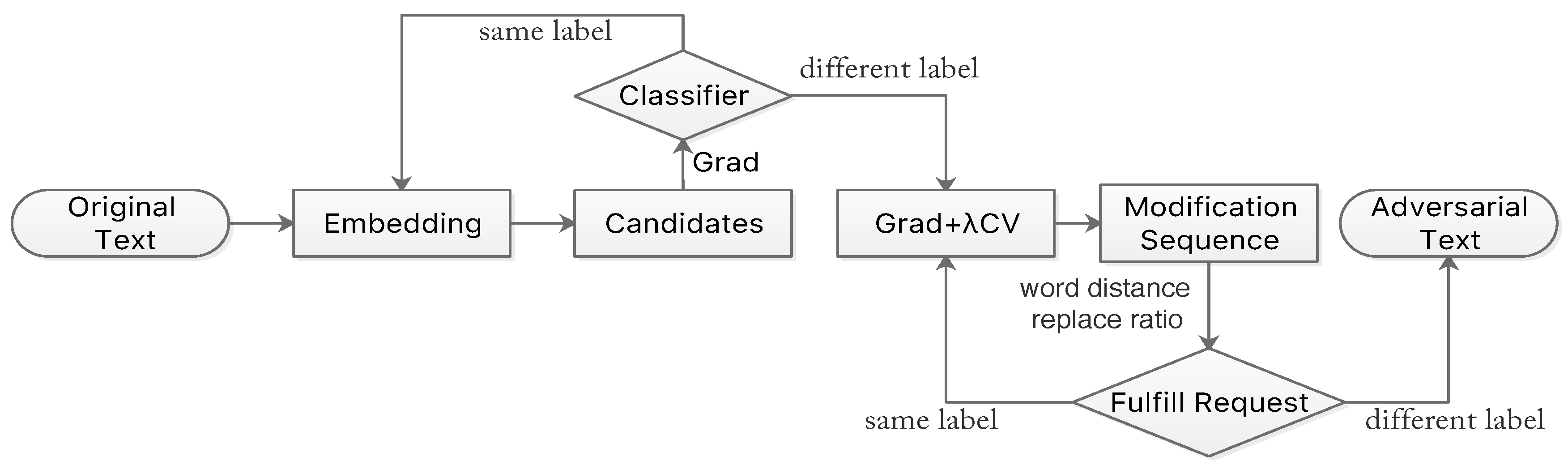
Applied Sciences | Free Full-Text | A Hybrid Adversarial Attack for Different Application Scenarios | HTML

Tricking a Machine into Thinking You're Milla Jovovich | by Rey Reza Wiyatno | Element AI Lab | Medium
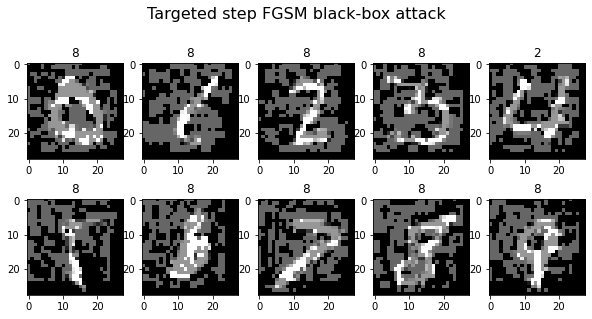
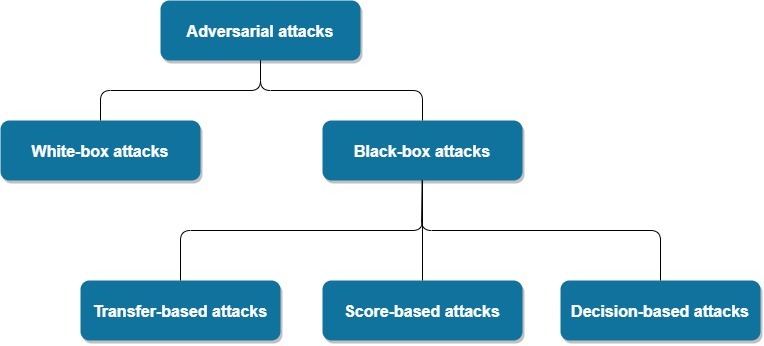
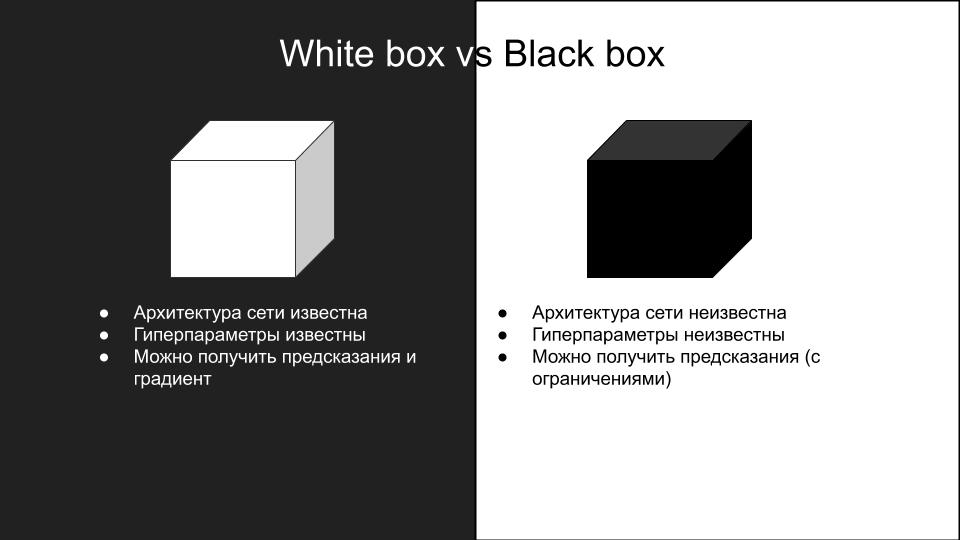
Institute for Applied AI - Selected Topics in Deep Learning - #1 Adversarial Attacks: C3 Black-Box Attacks

Black Box Attack Watches inputs and outputs Controls input text ... | Download Scientific Diagram

Implementation of White-Box Cryptography in Credit Card Processing Combined with Code Obfuscation | Semantic Scholar







![PDF] Side-Channel Gray-Box Attack for DNNs | Semantic Scholar PDF] Side-Channel Gray-Box Attack for DNNs | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/46c83b8f59ec1507a931282288133415b7b5d8db/3-Figure1-1.png)

![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/2-Figure1-1.png)