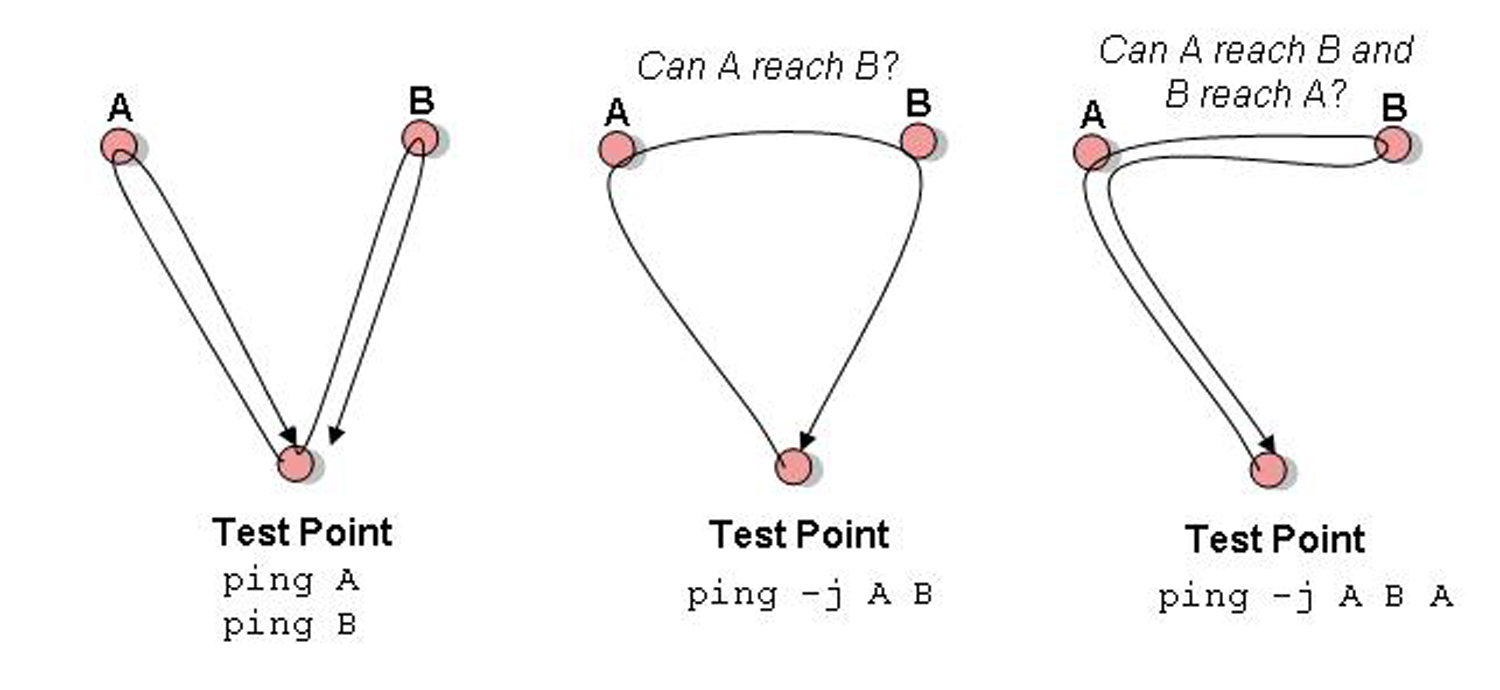
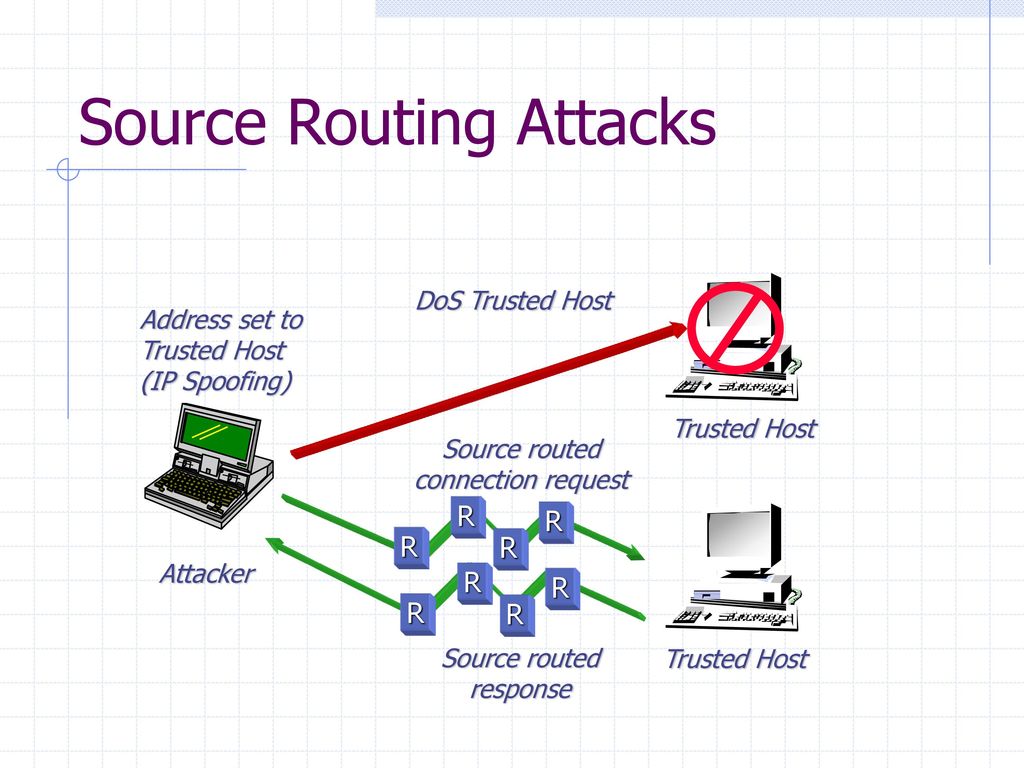
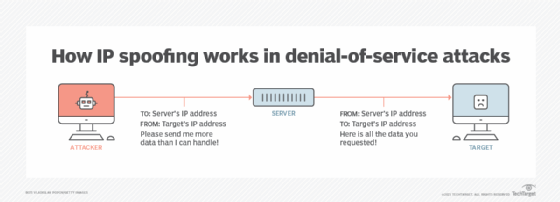
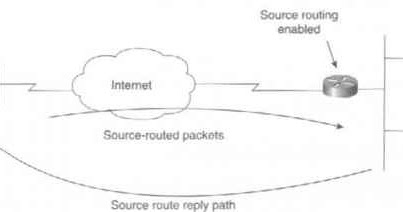
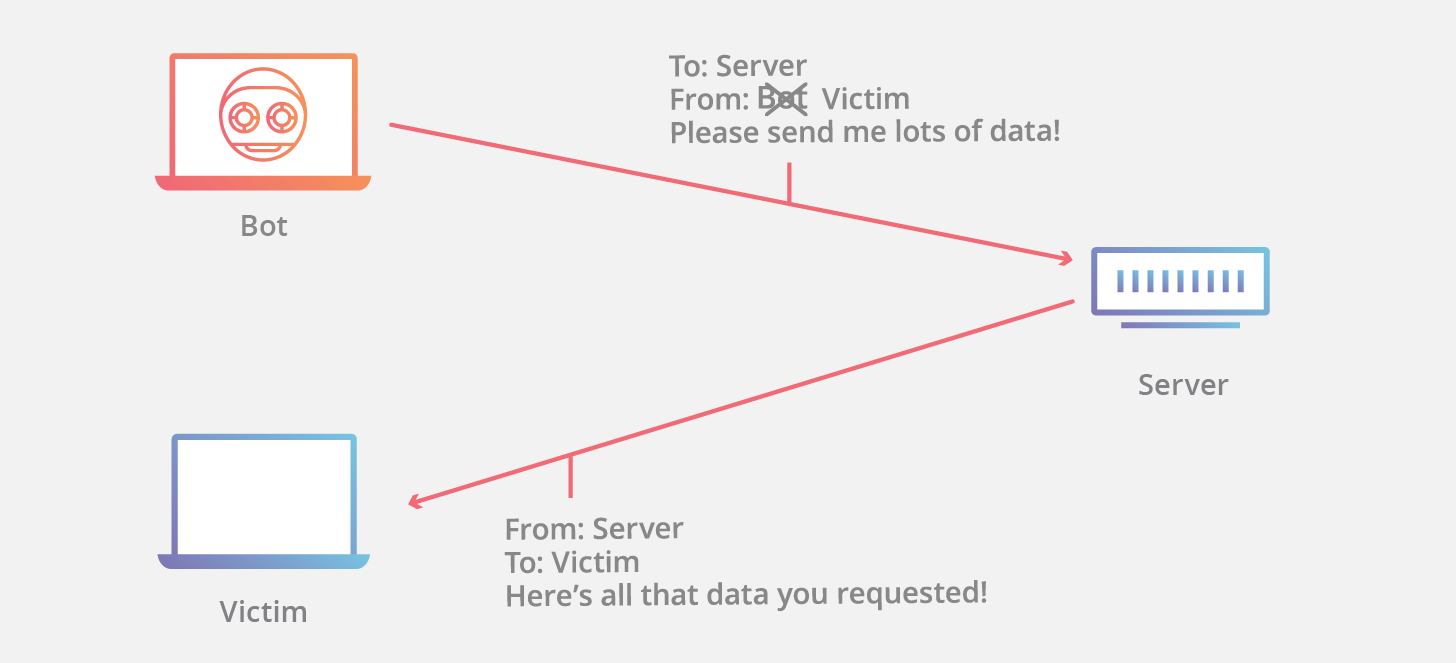
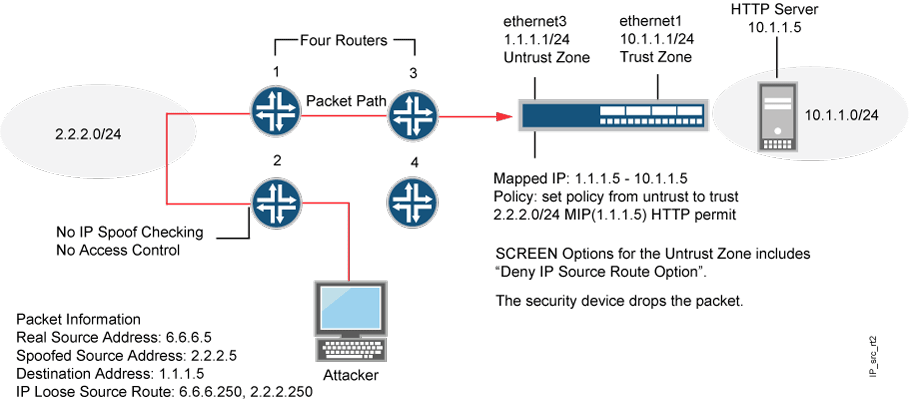
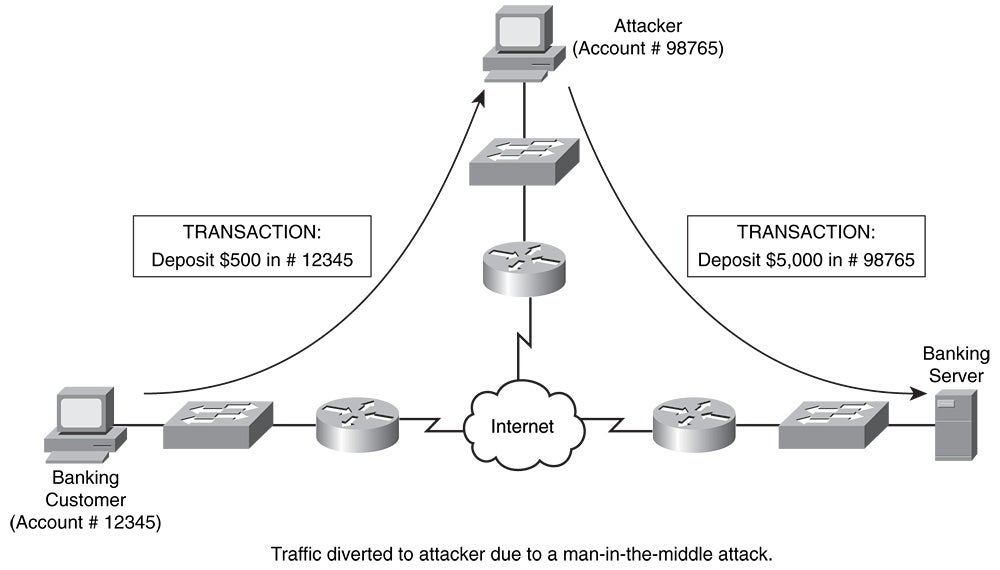
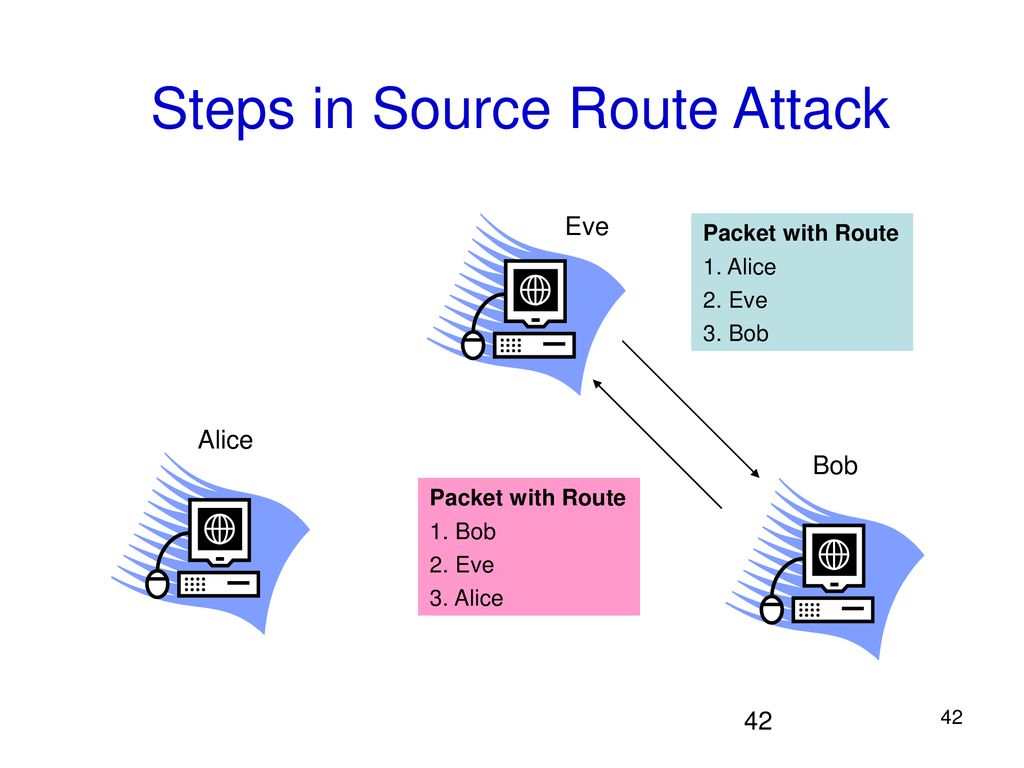
Malicious route construction attacks on source routing: carousel attack | Download Scientific Diagram

Trust Mechanisms to Secure Routing in Wireless Sensor Networks: Current State of the Research and Open Research Issues

Malicious route construction attacks on source routing: stretch attack | Download Scientific Diagram