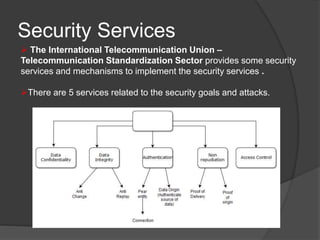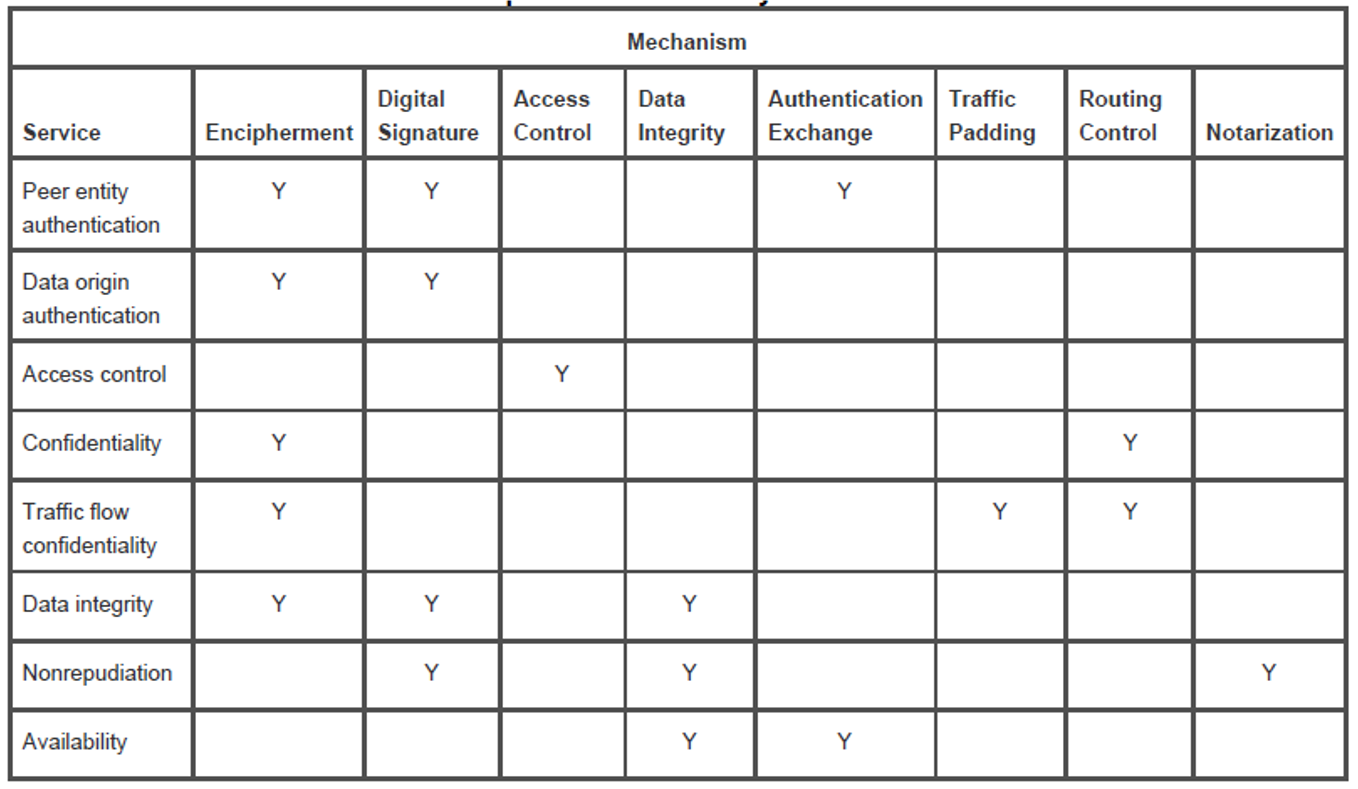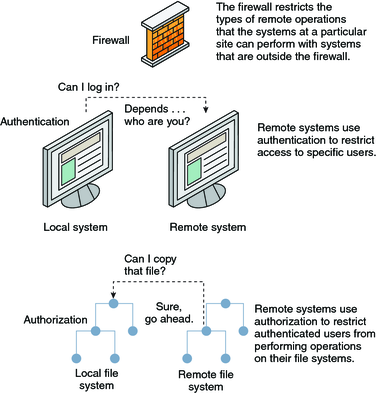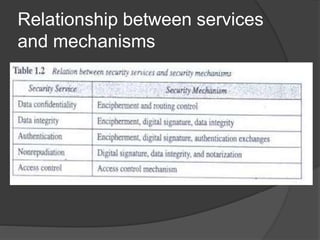
Sensors | Free Full-Text | Trust and Privacy Solutions Based on Holistic Service Requirements | HTML

02.Lecture-2-Security-Attacks-Services-and-Mechanisms.pdf - Lecture-02: Security Attacks, Services & Mechanism Prepared by: K M Akkas Ali, Assistant | Course Hero

Henric Johnson1 Network Security /. 2 Outline Attacks, services and mechanisms Security attacks Security services Methods of Defense A model for Internetwork. - ppt download

Table 3 from Trusted third party services for deploying secure telemedical applications over the WWW | Semantic Scholar

1 Introduction to Network Security Spring Outline Introduction Attacks, services and mechanisms Security threats and attacks Security services. - ppt download
CS480 Cryptography and Information Security Huiping Guo Department of Computer Science California State University, Los Angeles Course administration. - ppt download

Cryptography and Security Services: Mechanisms and Applications: Manuel Mogollon: 9781599048376: Books: Amazon.com