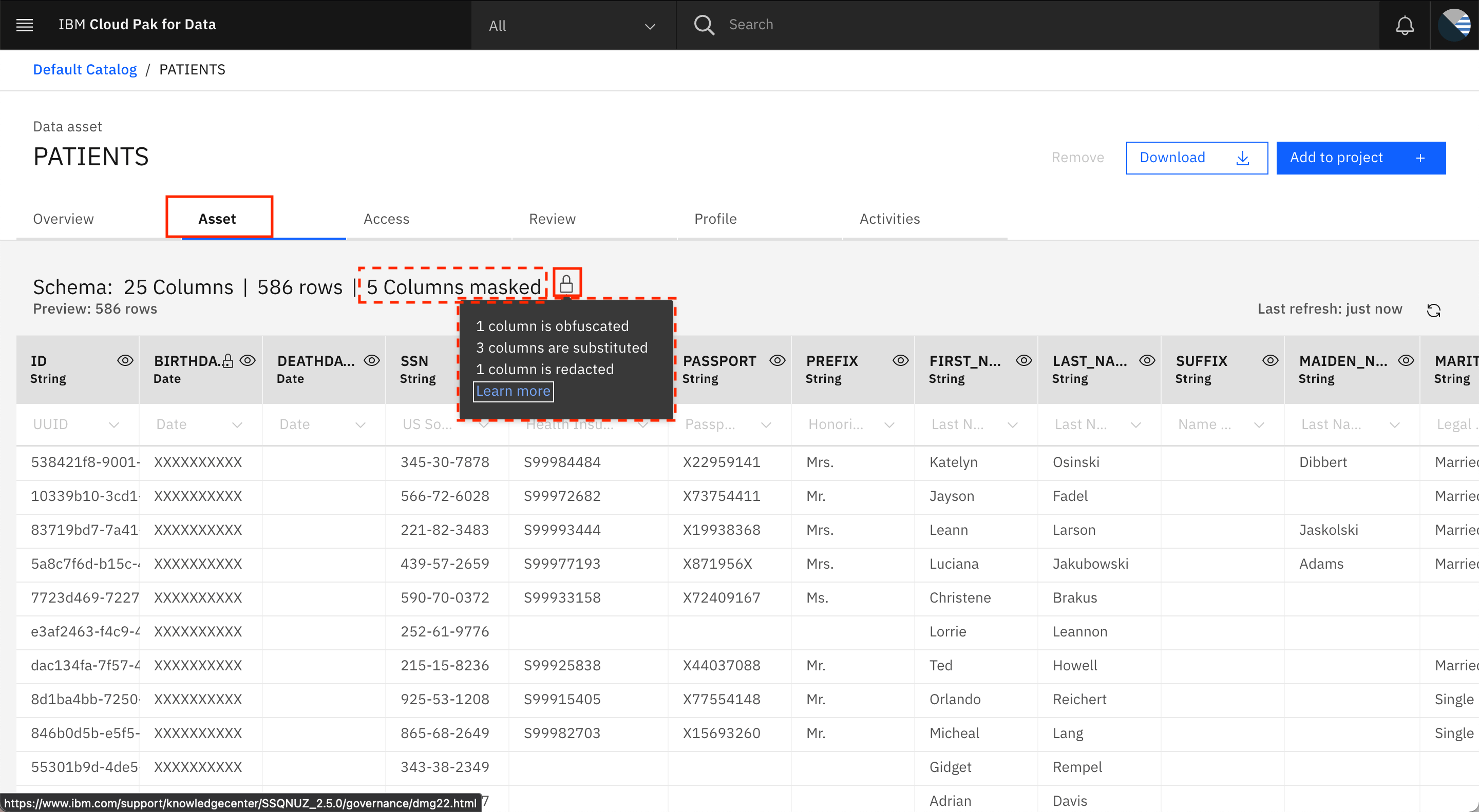
Microsoft Information Protection showcases integrated partner solutions at Microsoft Ignite - Microsoft Tech Community
Pattern to replace sensitive information in the message · Issue #79 · logfellow/logstash-logback-encoder · GitHub

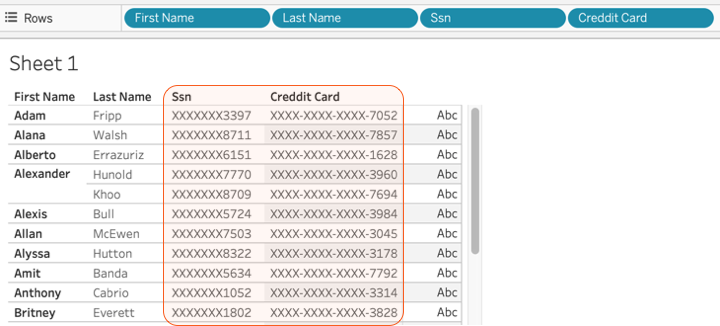
Part 4 – API Security Best Practices – Data Masking of sensitive data in OData / REST APIs | SAP Blogs