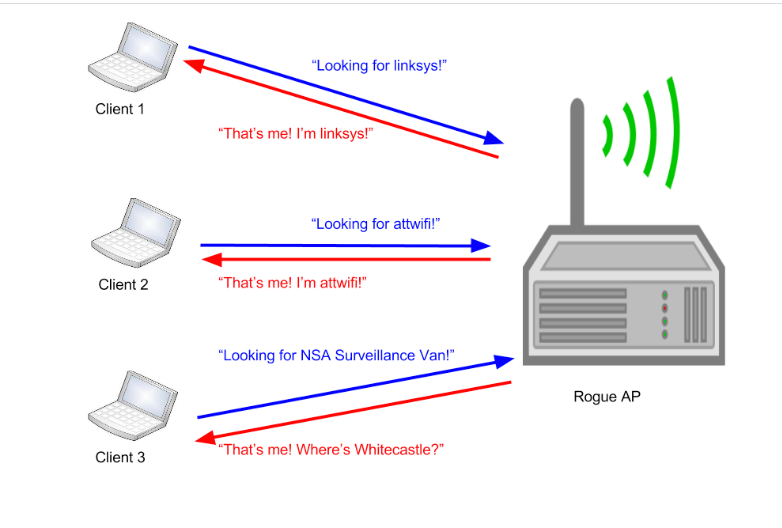
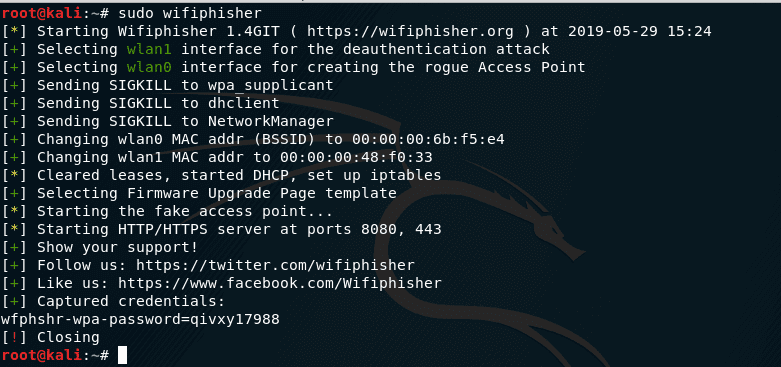
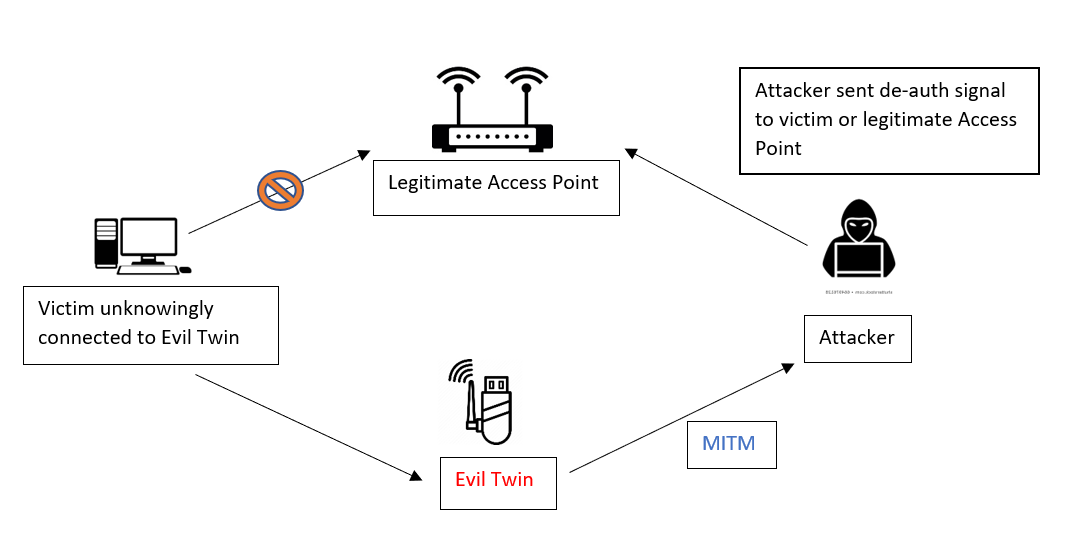
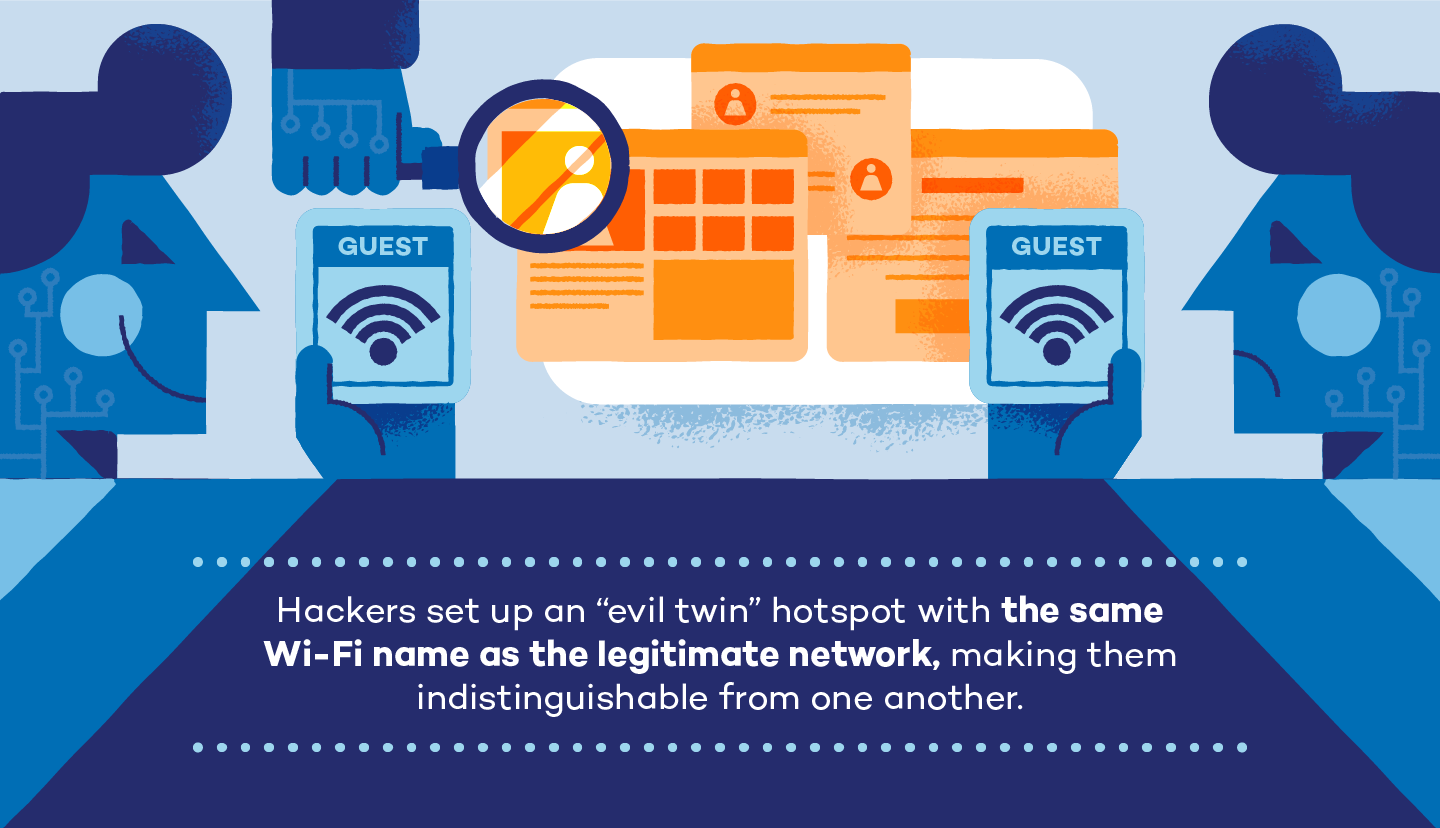
How to Hack Wi-Fi: Creating an Evil Twin Wireless Access Point to Eavesdrop on Data « Null Byte :: WonderHowTo

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

Hello, in this article you are going to learn how to hack wifi wpa/wap2 wps enabled or locked or unlocked or whatever net… | Wifi hack, Evil twin, Computer security

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library