Primer on GDPR Pseudonymization. Personal data is any information… | by Balaji Ramakrishnan | Medium

Taking charge of your data: using Cloud DLP to de-identify and obfuscate sensitive information | Google Cloud Blog

Informatica Persistent Data Masking VS Informatica Dynamic Data Masking - compare differences & reviews?

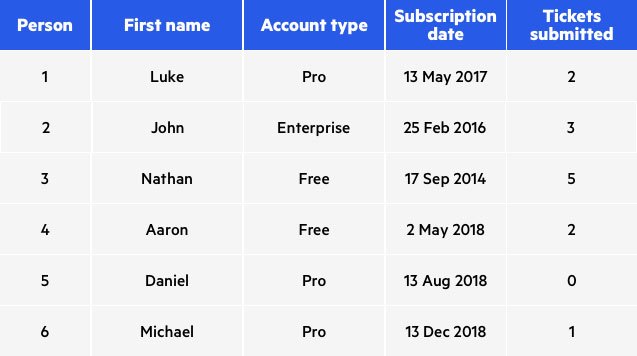
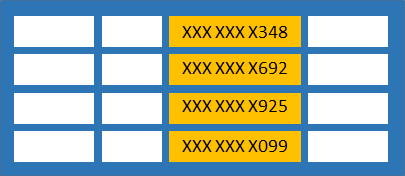
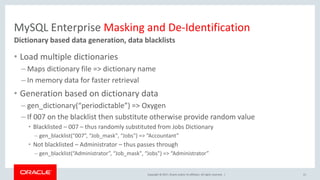
Data Masking Counter Attack to Identity Theft Paul Preston Data Masking: Counter Attack to Identity Theft. - ppt download