
Comparison of different Access Control Mechanisms in a cloud environment. | Download Scientific Diagram

ICS Information Security Assurance Framework 18 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Access Control Mechanism that Scanning a Bar Code on a Paper Ticket, Security Concept. Media. Close Up for a Man Hand in Editorial Stock Image - Image of alarm, asian: 154884064

A decentralized access control mechanism using authorization certificate for distributed file systems | Semantic Scholar




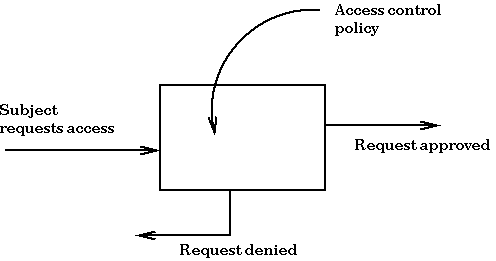

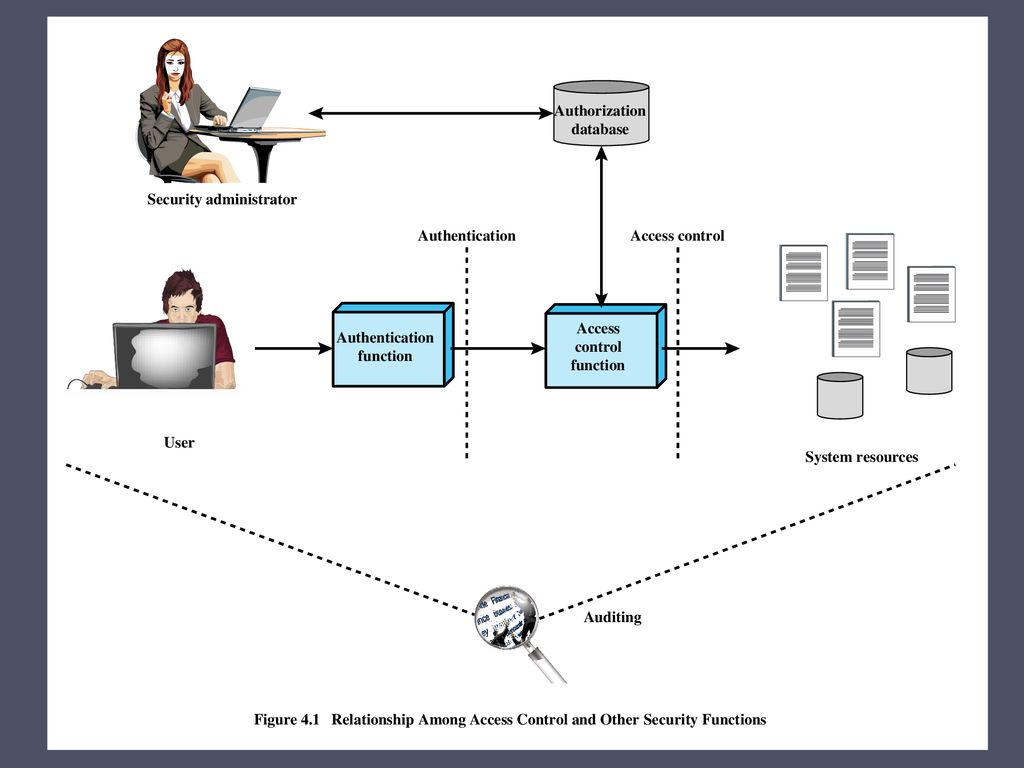



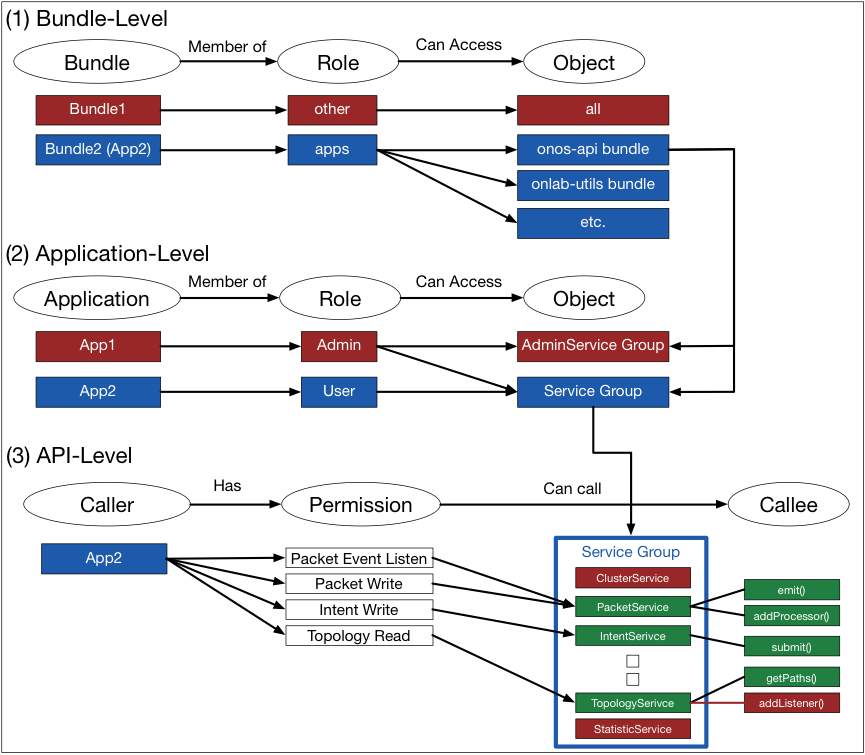





/An%20open%20source%20policy%20language%20for%20Attribute-Stream%20Based%20Access%20Control%20(ASBAC)/attribute-based_access_control_mechanism.png)




